Solarwinds Identity Monitor
Get notified whenever corporate credentials appear in a data leak and stop account takeover attempts
Overview:
SolarWinds Identity Monitor lets you know when your employee’s credentials appear in data breaches. This enables you to take action to protect your organization, preventing bad actors from accessing your systems and data.
A team of skilled researchers continuously collects credentials from data leaks from across the dark web, processes the data, and notifies if something associated with your monitored domains appear in a data breach.
Identity Monitor At A Glance
- Monitoring employee email addresses for exposure from data breaches
- Past breach history with timeline and details
- Employee private email address monitoring—for high-impact employees or board members
- IP address monitoring (available from certain licensing tiers)
Features:
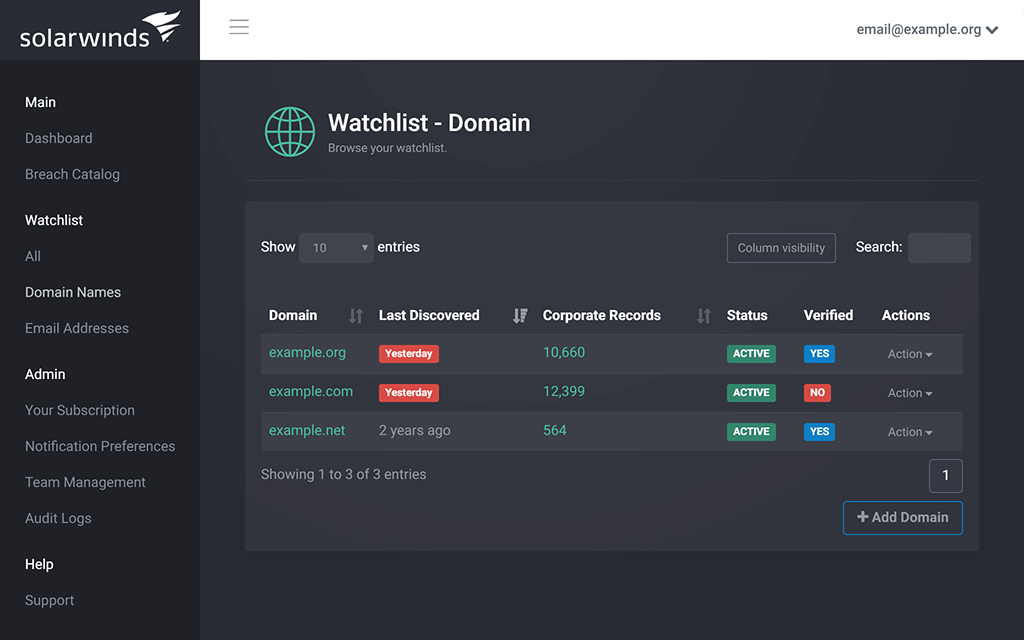
- Email Domain Watchlist
Add one or more domains to the watchlist and get notified whenever associated credentials are found in a newly identified data breach. - Historic Exposure Check
Access to all identified historic records of credential exposure for your monitored domains. - Private Email Address Monitoring
With Identity Monitor you can add private email addresses to the watchlist, and you’ll get notified of any compromise to prevent common phishing attacks, such as an urgent email from a key executive disrupting employee productivity. - Comprehensive Breach Database
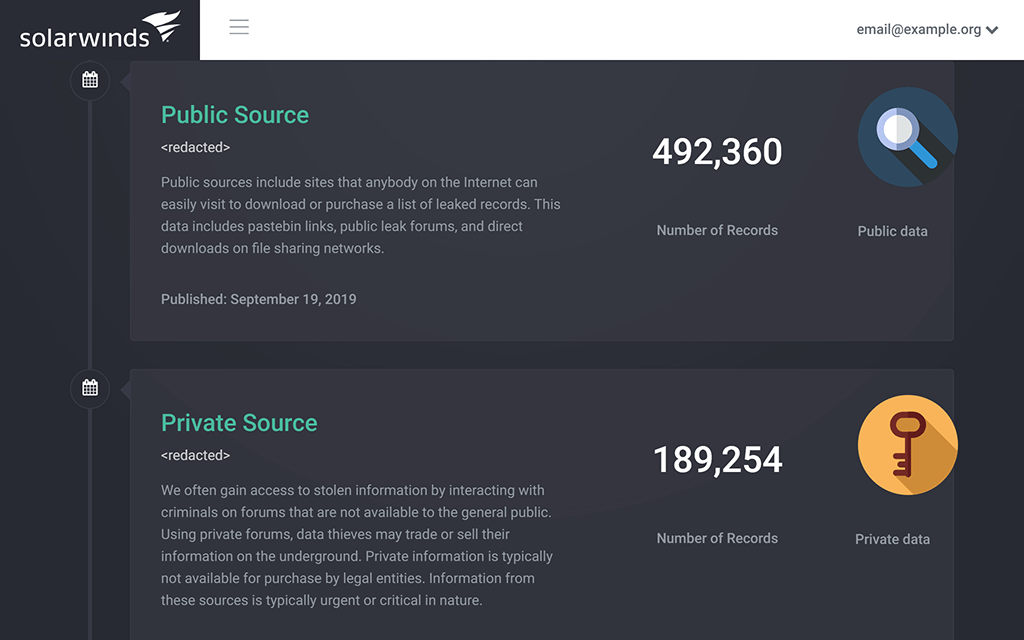
Security researchers, who discover data breaches all around the clear web, deep web, and dark web, constantly add and process compromised credentials. The freshness and timeliness are a key advantage and distinction to similar products. - IP Address Monitoring
In addition to email domains, from certain subscription tiers, you can add an IPv4 Address or IPv4 Network CIDR to your watchlist to be monitored for exposure in botnets and breaches. If an IP address is matched with a botnet, it might indicate an employee has active credential stealing malware on their computer. If a monitored IP address shows up in a breach, it’s typically because the exposed data contains the last logon IP of a user. - More Than Credential
Depending on the data breach, Identity Monitor can display more information. For example, the password encryption type (or lack thereof in case of plain-text leaked passwords), salt, account signup time, and personally identifiable information associated with the data breach. - Domain Verification
We use various methods to verify domain ownership, so only your organization can add a domain to the watchlist and access the breach history
Screenshots:
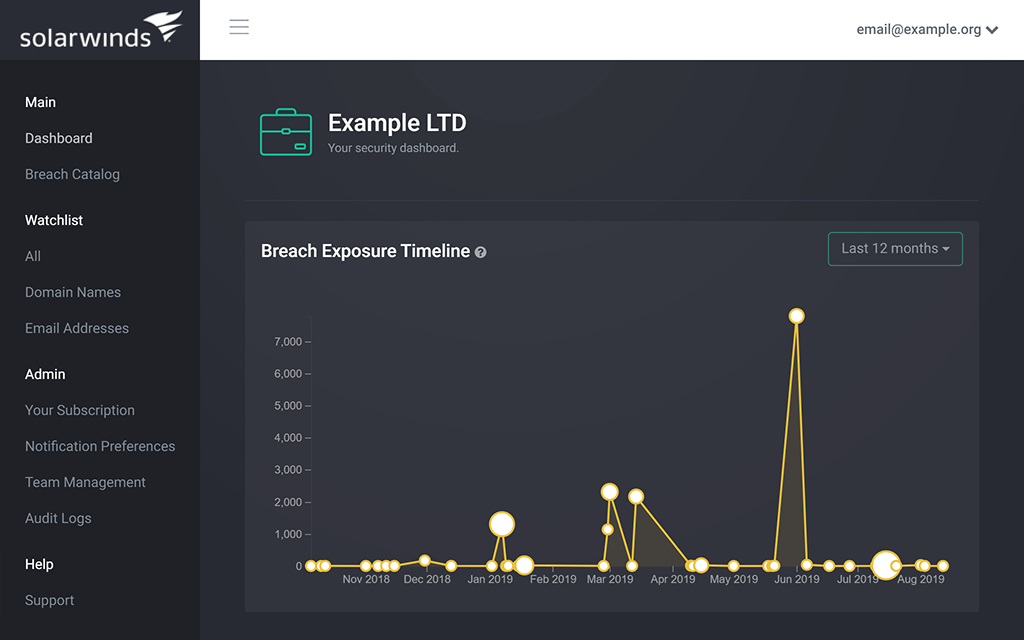
Account Takeover Prevention
Get notified whenever your monitored domains show up in a credentials data leak.
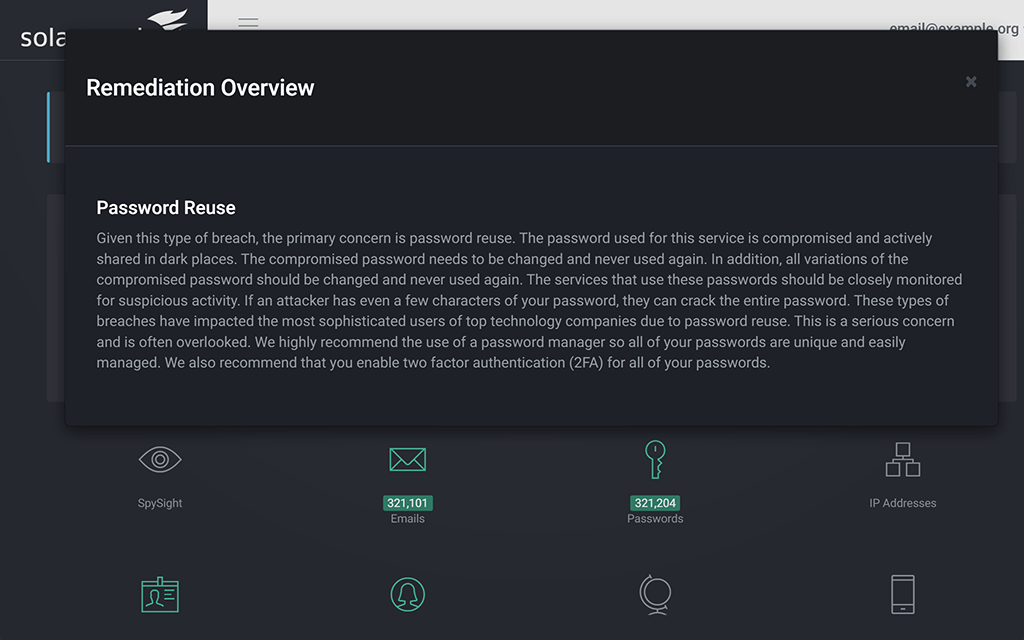
Compromised Account Detection
Improve business safeguards with compromised account detection services.
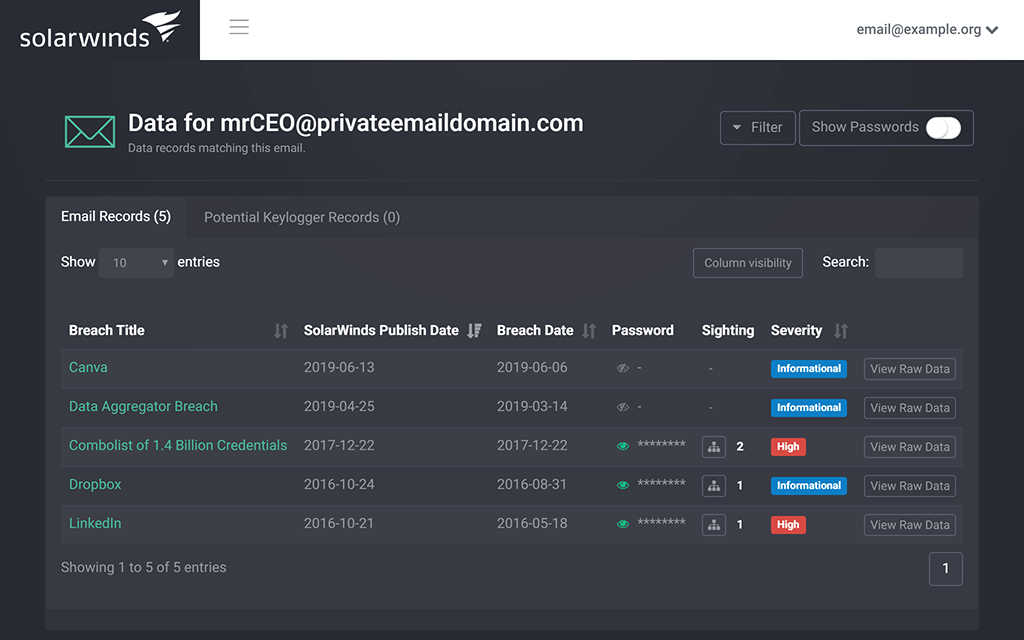
Detect Compromised Email Address
Check for exposed addresses and login information, so you can update passwords quickly to minimize potential impact.
Multiple Monitored Domains
Monitor multiple email domains and IP addresses for exposure in a data breach.
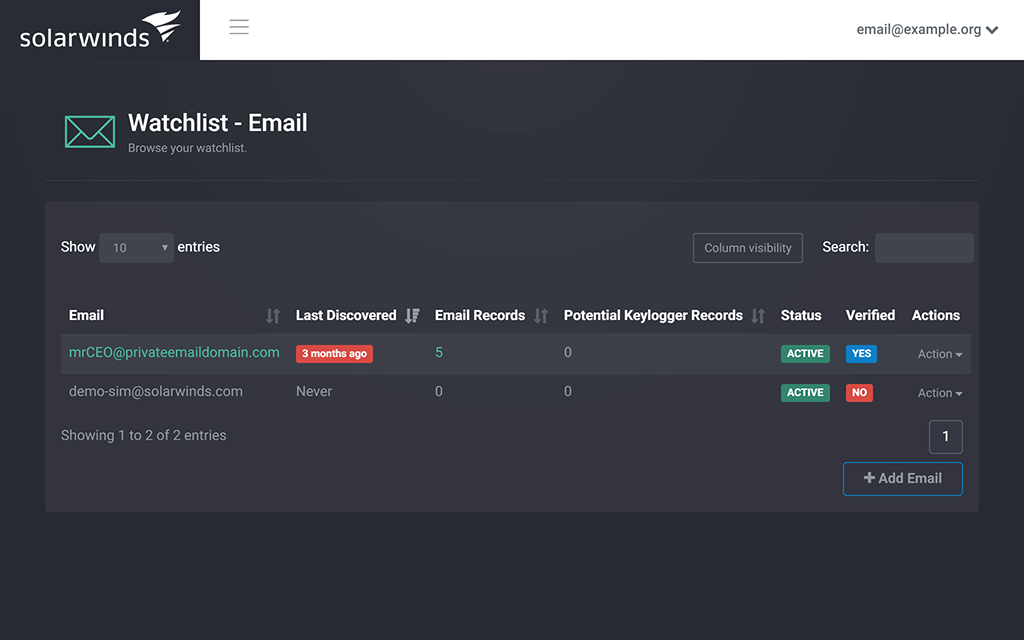
Private Email Monitoring
Monitor private email addresses of high-impact employees appearing in data leaks.
System Requirements:
Licensing
Identity monitor is a yearly subscription service. The subscription tiers are based on the number of employees in your organization, with higher tiers allowing more domains and IP address monitoring.
What is account takeover?
Account takeover (ATO) attacks are a form of identity theft using real credentials exposed by a security breach to gain access to corporate resources.
How does account takeover happen?
The core aspect of account takeover is bad actors using legitimate credentials found in data breaches to access corporate accounts and systems.
How do we collect data?
By leveraging the skills of human intelligence specialists and applied research, we find and flag breach data from public and non-public sources, where it’s often sold to users with malicious intent.
What types of information are we looking for?
Any compromised credentials (username and password) associated with a monitored domain or a monitored personal email address.
How often will I receive an alert?
Any time one of your credentials shows up, you’ll get an alert. A large enterprise can expect a few alerts each month. A smaller company can expect an alert every few months.
Can I try the product for free?
Yes. Just enter your work email address at the top of the page to see details of its exposure. You’ll start receiving notifications whenever it shows up in a new data leak. In addition, you can see the aggregate statistics about the data from the email address domain.
Documentation:
Download the Solarwinds Identity Monitor Datasheet (.PDF)
Get in touch with a Solarwinds Solutions Specialist today to Learn More!